62 changed files with 223 additions and 1228 deletions
+ 0
- 0
docs/docs/guides/developer-guide/error-handling.md → docs/docs/guides/advanced-topics/error-handling.md
+ 0
- 0
docs/docs/guides/developer-guide/logging.md → docs/docs/guides/advanced-topics/logging.md
+ 0
- 0
docs/docs/guides/developer-guide/promotions.md → docs/docs/guides/developer-guide-old/promotions.md
+ 0
- 0
docs/docs/guides/developer-guide/shipping.md → docs/docs/guides/developer-guide-old/shipping.md
+ 0
- 0
docs/docs/guides/developer-guide/stand-alone-scripts.md → docs/docs/guides/developer-guide-old/stand-alone-scripts.md
+ 0
- 0
docs/docs/guides/developer-guide/taxes.md → docs/docs/guides/developer-guide-old/taxes.md
+ 0
- 0
docs/docs/guides/developer-guide/testing.md → docs/docs/guides/developer-guide-old/testing.md
+ 0
- 0
docs/docs/guides/developer-guide/translations.md → docs/docs/guides/developer-guide-old/translations.md
+ 0
- 0
docs/docs/guides/developer-guide/updating-vendure.md → docs/docs/guides/developer-guide-old/updating-vendure.md
+ 0
- 0
docs/docs/guides/developer-guide/uploading-files.md → docs/docs/guides/developer-guide-old/uploading-files.md
+ 0
- 0
docs/docs/guides/developer-guide/vendure-worker.md → docs/docs/guides/developer-guide-old/vendure-worker.md
+ 0
- 453
docs/docs/guides/developer-guide/authentication.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
BIN
docs/docs/guides/developer-guide/channels/channels_currencies_diagram.png

BIN
docs/docs/guides/developer-guide/channels/channels_diagram.png

BIN
docs/docs/guides/developer-guide/channels/channels_prices_diagram.png

+ 0
- 69
docs/docs/guides/developer-guide/channels/index.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 0
- 0
docs/docs/guides/getting-started/configuration.md → docs/docs/guides/developer-guide/configuration/index.md
+ 0
- 0
docs/docs/guides/concepts/custom-fields/custom-fields-data-table.webp → docs/docs/guides/developer-guide/custom-fields/custom-fields-data-table.webp

+ 0
- 0
docs/docs/guides/concepts/custom-fields/custom-fields-ui.webp → docs/docs/guides/developer-guide/custom-fields/custom-fields-ui.webp

+ 0
- 0
docs/docs/guides/concepts/custom-fields/index.md → docs/docs/guides/developer-guide/custom-fields/index.md
BIN
docs/docs/guides/developer-guide/customizing-the-order-process/custom-order-ui.webp

+ 0
- 173
docs/docs/guides/developer-guide/customizing-the-order-process/index.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 0
- 0
docs/docs/guides/concepts/data-model/admin-role.webp → docs/docs/guides/developer-guide/data-model/admin-role.webp

+ 0
- 0
docs/docs/guides/concepts/data-model/channels.webp → docs/docs/guides/developer-guide/data-model/channels.webp

+ 0
- 0
docs/docs/guides/concepts/data-model/collection-filters.webp → docs/docs/guides/developer-guide/data-model/collection-filters.webp

+ 0
- 0
docs/docs/guides/concepts/data-model/collections.webp → docs/docs/guides/developer-guide/data-model/collections.webp
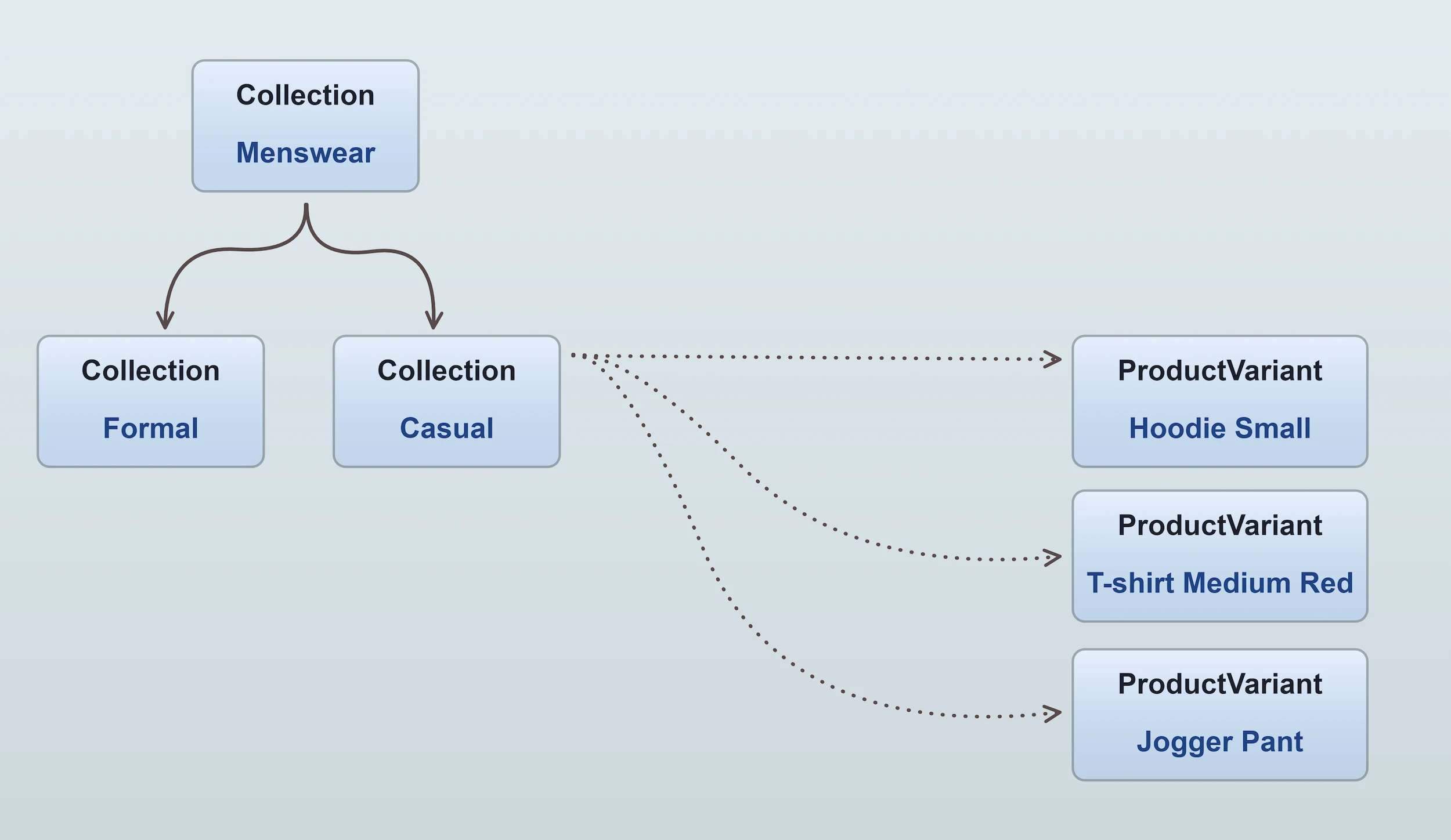
+ 0
- 0
docs/docs/guides/concepts/data-model/customer.webp → docs/docs/guides/developer-guide/data-model/customer.webp

+ 0
- 0
docs/docs/guides/concepts/data-model/facets.webp → docs/docs/guides/developer-guide/data-model/facets.webp

+ 1
- 1
docs/docs/guides/concepts/data-model/index.mdx → docs/docs/guides/developer-guide/data-model/index.mdx
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 0
- 0
docs/docs/guides/concepts/data-model/order.webp → docs/docs/guides/developer-guide/data-model/order.webp

+ 0
- 0
docs/docs/guides/concepts/data-model/products-variants.webp → docs/docs/guides/developer-guide/data-model/products-variants.webp

+ 0
- 9
docs/docs/guides/developer-guide/developer-guide.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 0
- 59
docs/docs/guides/developer-guide/job-queue/index.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
BIN
docs/docs/guides/developer-guide/job-queue/job_queue_req_res.png

BIN
docs/docs/guides/developer-guide/job-queue/job_queue_req_res_with_queue.png

BIN
docs/docs/guides/developer-guide/job-queue/job_queue_sequence.png

+ 0
- 107
docs/docs/guides/developer-guide/migrations.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 221
- 0
docs/docs/guides/developer-guide/migrations/index.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
BIN
docs/docs/guides/developer-guide/migrations/migration.webp

+ 0
- 0
docs/docs/guides/getting-started/overview/Vendure_docs-architecture.webp → docs/docs/guides/developer-guide/overview/Vendure_docs-architecture.webp

+ 0
- 0
docs/docs/guides/getting-started/overview/index.md → docs/docs/guides/developer-guide/overview/index.md
+ 0
- 293
docs/docs/guides/developer-guide/payment-integrations/index.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
BIN
docs/docs/guides/developer-guide/payment-integrations/payment_sequence_one_step.png

BIN
docs/docs/guides/developer-guide/payment-integrations/payment_sequence_two_step.png

+ 0
- 0
docs/docs/guides/concepts/plugins/index.mdx → docs/docs/guides/developer-guide/plugins/index.mdx
BIN
docs/docs/guides/developer-guide/stock-control/global-stock-control.webp

+ 0
- 63
docs/docs/guides/developer-guide/stock-control/index.md
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 0
- 0
docs/docs/guides/concepts/strategies-configurable-operations/collection-filters-args.webp → docs/docs/guides/developer-guide/strategies-configurable-operations/collection-filters-args.webp

+ 0
- 0
docs/docs/guides/concepts/strategies-configurable-operations/collection-filters.webp → docs/docs/guides/developer-guide/strategies-configurable-operations/collection-filters.webp

+ 0
- 0
docs/docs/guides/concepts/strategies-configurable-operations/index.mdx → docs/docs/guides/developer-guide/strategies-configurable-operations/index.mdx
+ 0
- 0
docs/docs/guides/concepts/the-api-layer/Vendure_docs-api_request.webp → docs/docs/guides/developer-guide/the-api-layer/Vendure_docs-api_request.webp

+ 0
- 0
docs/docs/guides/concepts/the-api-layer/index.mdx → docs/docs/guides/developer-guide/the-api-layer/index.mdx
+ 0
- 0
docs/docs/guides/concepts/the-service-layer/index.mdx → docs/docs/guides/developer-guide/the-service-layer/index.mdx
+ 0
- 0
docs/docs/guides/concepts/worker-job-queue/Vendure_docs-job-queue-2.webp → docs/docs/guides/developer-guide/worker-job-queue/Vendure_docs-job-queue-2.webp
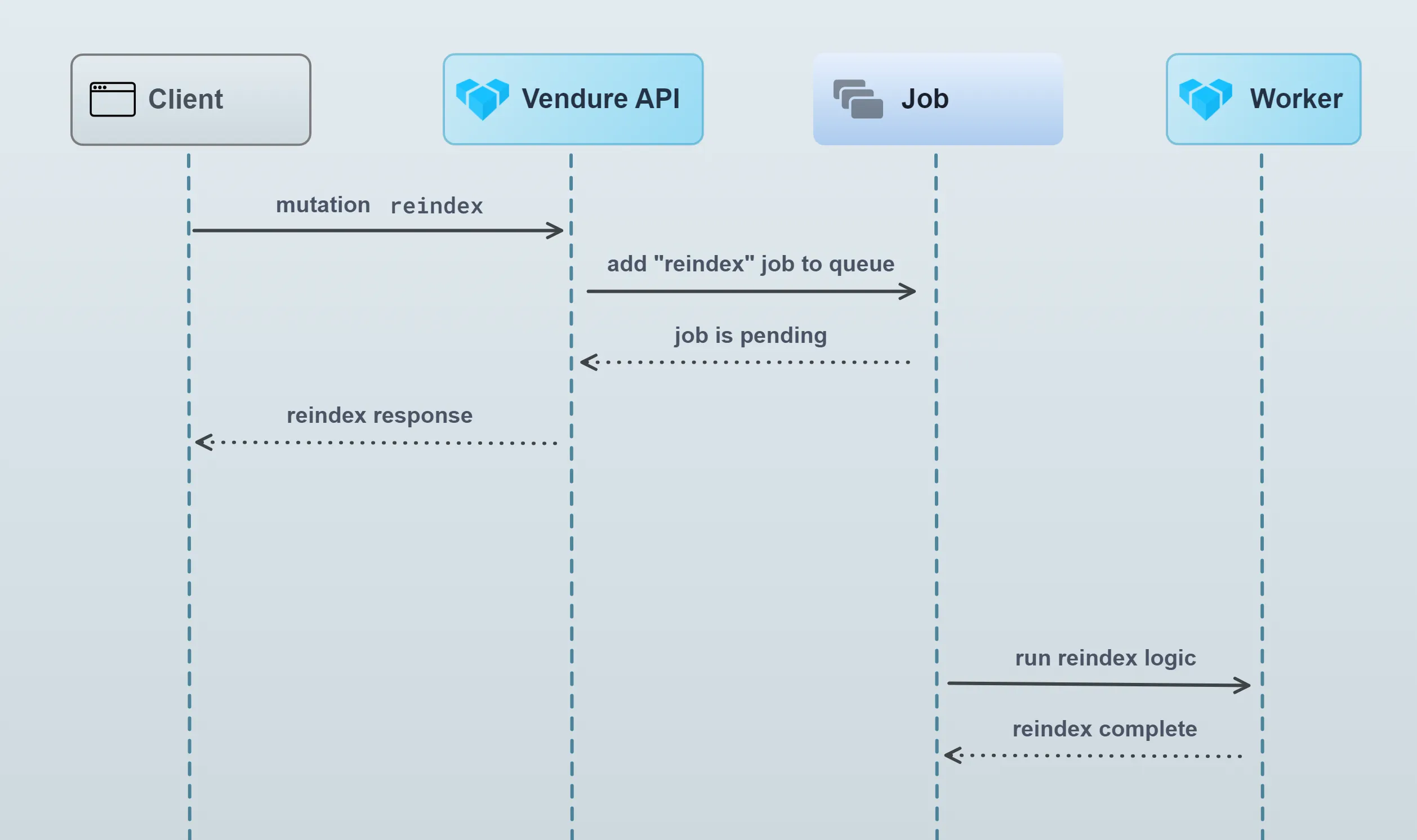
+ 0
- 0
docs/docs/guides/concepts/worker-job-queue/Vendure_docs-job-queue-3.webp → docs/docs/guides/developer-guide/worker-job-queue/Vendure_docs-job-queue-3.webp

+ 0
- 0
docs/docs/guides/concepts/worker-job-queue/Vendure_docs-job-queue.webp → docs/docs/guides/developer-guide/worker-job-queue/Vendure_docs-job-queue.webp

+ 0
- 0
docs/docs/guides/concepts/worker-job-queue/index.mdx → docs/docs/guides/developer-guide/worker-job-queue/index.mdx
+ 0
- 0
docs/docs/guides/concepts/worker-job-queue/worker-job-queue.webp → docs/docs/guides/developer-guide/worker-job-queue/worker-job-queue.webp

+ 0
- 0
docs/docs/guides/developer-guide/importing-product-data.md → docs/docs/guides/how-to/importing-product-data.md
+ 0
- 0
docs/docs/guides/developer-guide/multi-vendor-marketplaces/aggregate-order.webp → docs/docs/guides/how-to/multi-vendor-marketplaces/aggregate-order.webp

+ 0
- 0
docs/docs/guides/developer-guide/multi-vendor-marketplaces/index.md → docs/docs/guides/how-to/multi-vendor-marketplaces/index.md
+ 1
- 1
packages/core/src/config/order/order-item-price-calculation-strategy.ts
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||